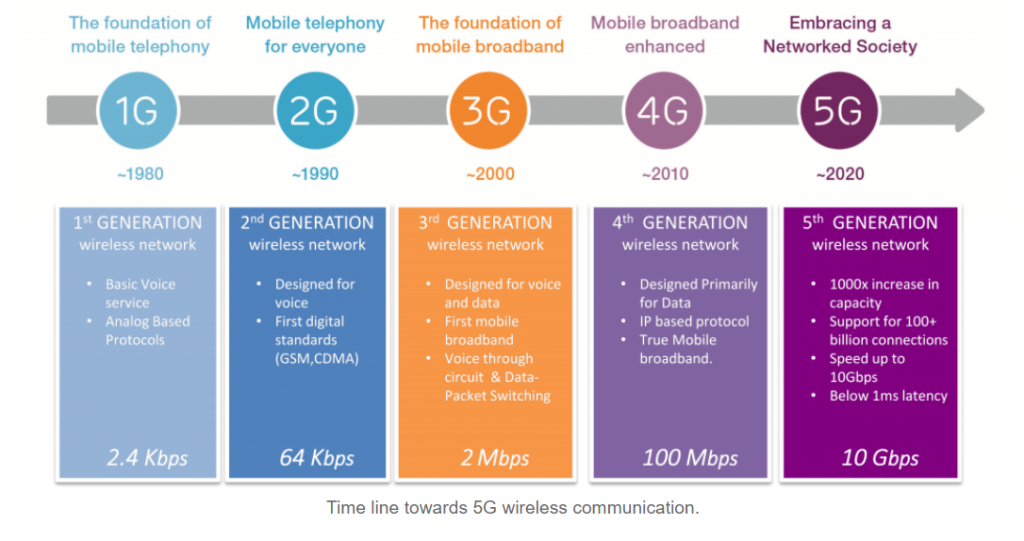
5G is a new global wireless standard after 1G, 2G, 3G, and 4G networks. 5G enables a new kind of network designed to connect everyone virtually, including machines, objects, and devices.
5G wireless technology is meant to deliver higher multi-Gbps peak data speeds, ultra-low latency, more reliability, massive network capacity, increased availability, and a more consistent user experience to more users. Higher performance and improved efficiency empower new user experiences and connect new industries.
It is 100 times faster than 4G and 5G is creating never-before-seen opportunities for people and businesses. 5G runs on the same radio frequencies that are currently being used for your smartphone, on Wi-Fi networks and in satellite communications, but it enables technology to go a lot further.
Evolution--
what makes 5G different?
5G Capabilities Wide-range of other sectors will experience dramatic transformation, underpinned by entirely new 5G-enabled mobile capabilities.
Examples include:
The ability to start streaming large volumes of HD audio & visual content in no time.
Lag-free networks with very high reliability and availability, enable remote operations and robotics for even the most critical applications.
The ability to create multiple virtual networks on-demand, each with its performance and security specifications – called network slicing.
A shift to more cloud-based services will improve access to resources via edge computing, making data processing and storage more efficient.
How does this work--
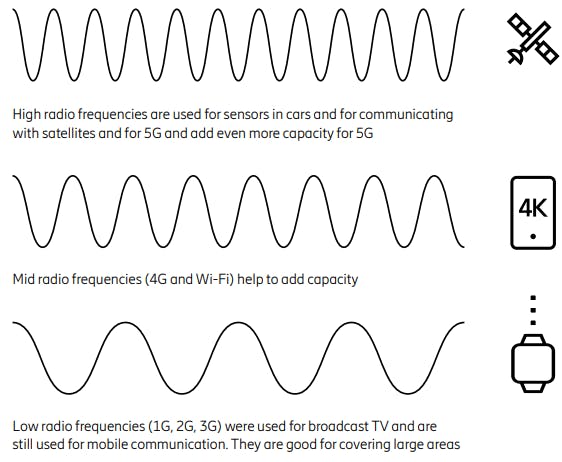
Mobile networks use radio waves to communicate, radio waves have different frequencies and 5G uses three different ranges of radio frequency – low, mid and high.
Whereas 2G, 3G and 4G were primarily radio focused, 5G represents an entire system with radio, a telecom core, and operating systems all transformed to support new requirements. This process will involve new radio technologies, a virtualized cloud-based core, and end-to-end management to facilitate automation and new concepts like network slicing.
Applications of 5G-
Enhanced Mobile Broadband: Mobile broadband is the first real use case for 5G, addressing traffic growth demands while also providing the higher quality of experience that consumers increasingly expect.
Fixed Wireless Access: 5G fixed wireless access effectively eliminates the need for costly deployment of deep-fibre fixed access infrastructure, while offering peak rates that few fixed technologies are able to match.
Massive Internet Of Things: Massive IoT, as the name suggests, is less about speed and more about scale. It refers to applications requiring connectivity over large areas involving a huge volume of connections and devices. Typically, connections are transmitting low-volume, non-critical data.
Broadband Internet Of Things: Broadband IoT takes things up a level from Massive IoT. It adopts the capabilities of mobile broadband connectivity, providing much higher data rates and lower latencies than Massive IoT. It does this while using machine functionalities for coverage extension and extended device battery life.
Industrial Internet of Things: Industrial Automation IoT will enable advanced industrial automation applications with extremely demanding connectivity requirements. In some industrial deployments, wired networks may migrate to wireless connectivity in such a manner that different parts of an industrial system may switch to wireless connectivity gradually over time.
Will the 5G technology be secure?
4G networks use the USIM application to perform strong mutual authentication between the user and their connected device and the networks. The entity hosting the USIM application can be a removable SIM card or an embedded UICC chip.
This strong mutual authentication is crucial to enable trusted services.
Several security frameworks may co-exist in the future, and 5G is likely to re-use existing solutions used today for 4G networks and the cloud (SEs, HSM, certification, Over-The-Air provisioning, and KMS).
The standard for strong mutual authentication for 5G networks was finalized in 2018.
The need for 5G security, privacy, and trust will be as strong as for 4G, if not stronger, with the increased impact of IoT services.
Local SEs in devices can secure network access and support security services such as emergency call management and virtual IoT networks. Additionally, these older technologies cannot meet today's challenges of auditable compliance and the not-so-distant future's quantum threat challenges. Security, performance, interoperability, and auditable compliance are just a few of the 5G challenges that require immediate attention.
Finally, There is a need for a more intelligent data-in-motion security solution to accommodate the diverse range of 5G use cases.
